MAC randomization sounds more like what would happen at your neighborhood fast food joint than a cause for rumblings throughout the IT crowd. But it’s true. Apple announced a new privacy feature with the latest Apple iOS 14, iPadOS 14, and watchOS 7 using MAC randomization. To understand why this is making waves with IT professionals, we need to get a little nerdy here.
MAC randomization sounds more like what would happen at your neighborhood fast food joint than a cause for rumblings throughout the IT crowd. But it’s true. Apple announced a new privacy feature with the latest Apple iOS 14, iPadOS 14, and watchOS 7 using MAC randomization. To understand why this is making waves with IT professionals, we need to get a little nerdy here.
Medium Access Control (MAC, also called Media Access Control) addresses are how devices, wired and wireless, interact with the medium where they intend to send traffic. That medium can be a copper cable, a fiber optic cable, or a radio. This medium, whatever form it takes, it known as the Physical Layer in the OSI model. The MAC address is used in the Data Layer.
As we become a more mobile society, gone are the days of only being able to access information from specific places, like a desk or a kiosk. Today, we are constantly moving; around a city or town, or just from one room in the house to another. As devices move, the Physical Layer is constantly adjusting based on the situation. A laptop might be wired to the network during the morning and later be wireless while you work on your porch. The ability of the Physical Layer to adjust to our lifestyle means the Data Layer has taken on a much bigger role. It’s always been required to make network communications work, like all of the layers, but with the variability of the Physical Layer, network engineers have come to rely on the unchanging nature of the Data Layer as a way to keep networks stable. This sometimes comes to the detriment of the end-user. More on that later.
Figure 1 OSI Model
The key to network stability
To understand why we think of Layer 2, where the MAC address lives, as the key to network stability, we need to look at Layer 3, the Network Layer. This is where IP addresses live. IP addresses can change all the time. For different Wi-Fi networks, it’s almost a given it will change. From home to coffee shop to office to grocery store and back home, the Network Layer changes at each location. Even though it’s usually Wi-Fi in all of these places, the Physical Layer is also different: different bands, different channels, different settings, but still Wi-Fi.
CLICK TO TWEET: CommScope’s Jim Palmer explains why MAC Randomization is a big deal.
With all this fluctuation at Layers 1 & 3, network engineers have come to rely on the stability of Layer 2 and the MAC address to build stable networks. The benefit for the end user is obvious: network stability. The downside to this stability, for that same user, is that network operators can get to know that user’s habits through this stable piece of information. Network operators know when and how many times that same MAC address shows up at a particular store. If they can get the user of that device to provide some personal information—for instance by using a social media account to login to a captive portal—they can then tie those two pieces of information together. Tie MAC address to the user’s name and social media account and a whole new world opens up. Granted, that world might be from the movie “Minority Report” but it’s a game changer!
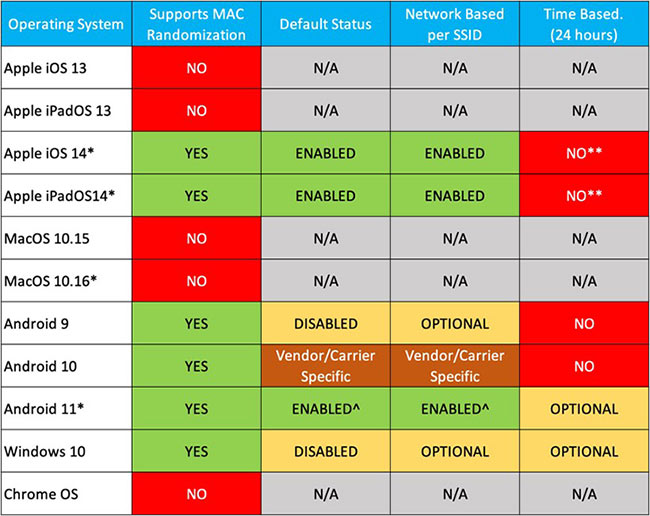
Welcome to the world of random MAC addresses. These aren’t new, by the way. Devices started using random MAC addresses during the Wi-Fi probing process back in 2014. Both Android and Windows have been using random MAC addresses for both ‘probing for’ and ‘connecting to’ networks for a while, but only if enabled in the advanced settings. Now Apple is enabling random MAC addresses for everything the device does by default. To add even more randomness to this randomization is a feature that changes the random MAC address every 24 hours for the same network. This was going to be enabled by default in iOS 14 but was removed during beta testing. However, in Android 11 and Windows 10 this is an advanced feature that can be enabled by the end user. By following this trajectory, it isn’t hard to imagine that MAC randomization is going to be enabled by default on all devices in the not-too-distant future.
From a user’s point of view this might be welcome. Since the local coffee shop can’t tie any personal information to something that is always changing, user anonymity is back. Users can’t be tracked as they go about their day. But is that always a good thing?
Figure 2 Current as of September 2020
Think back to the last time you stayed at a hotel for a couple of days. You connected to their network, entered something into a splash page, and you were on your way. The next time you needed to use it there was no splash page. The network knew you’d already logged in because they tied the login to the device’s MAC address. If the MAC address is randomized and new, networks can’t know if that device had already signed in or not. Users are going to have to sign in again. And again. If the hotel limits the number of devices—previously tracked by MAC address—that can be used by each guest, what happens now?
Captive portals, reserved DHCP addresses, Access Control Lists (ACLs) at Layers 2 & 3, firewall rules, the list of impacted services and features that could break goes on and on.
Random MAC addresses aren’t all bad. In the world of Wi-Fi, everything engineers do is a balancing act, a trade-off. From the user’s point of view, it’s a tradeoff between anonymity and ease of access to a network. Granted, users can enable or disable this random MAC address feature but to do that for every network would be quite the chore. For network administrators, engineers, and architects, this means going through each network to ensure randomness at Layer 2 won’t significantly impact the networks, either when these new OS’s are released for everyone to upgrade to or when new devices are launched with the new OS pre-loaded. There is different behavior between an upgrade and pre-loaded on a new device. Bear with me while I explain this one.
If you have an iOS 13 device and upgrade to iOS 14 or Android 9 to Android 10, it’s not supposed to use randomized MAC addresses for any networks you previously joined. If it’s a new WLAN, it will try a randomized MAC for the first attempt. If the association fails, it’s supposed* to revert to the burned-in MAC. If you have an iOS 13 device and upgrade to iOS 14, and then forget a previously joined WLAN, it’s supposed* to behave as if it’s a new WLAN. Forgetting and rejoining a network is a common troubleshooting step for many (me included) and understanding the implication of random MACs is important for future troubleshooting for both users and IT staff.
If you buy a device that has iOS 14 or Android 10 pre-loaded, every WLAN will be treated as a new one, so it will try a random MAC address for every WLAN. If the association fails, it’s supposed* to revert back to the burned-in MAC and attempt again. Since it’s a new device, that doesn’t help much. The amount of confusion caused while troubleshooting a device that has used multiple MAC addresses while attempting to connect and access the network will increase the time to resolve EVERY trouble call. This is the gift that will keep on giving to the network administrators!
Hopefully by this point you are asking about the impact and how to mitigate it. I wish there were an easy answer, but there never is. The easiest solution is to ask everyone that will ever use your network to turn this feature off for any SSID you manage. While possible, it’s totally impracticable. Getting 100% of the users to do this will never happen. Even if you have a mobile device management (MDM) with every device using it AND they are all connected after the rollout, profiles could be pushed that turns random MAC addresses off. Possible, yes! Probable… no. What users CAN do 100% of the time is call the help desk when they can’t connect. Imagine the current call volume to a help desk exponentially increasing based on where devices and users fall into the chart above coupled with the increased time dedicated to every call. Is an organization ready to take that on?
Now that you have a better understanding of the why of randomized MAC addresses, you can read more about the impact on networks and how CommScope can assist in part 2 of this blog.
*Look for a future blog once new phones start shipping with this new operating system pre-installed.