The hyperbole surrounding the Internet of Things (IoT) is understandable given
forecasts project connected devices will triple from 11 billion today to 30 billion in 2020, and triple again to 80 billion by 2025. And while
77 percent of enterprises budgeted for an IoT project in 2017, many are still waiting for the IoT to demonstrate meaningful return on investment (ROI).
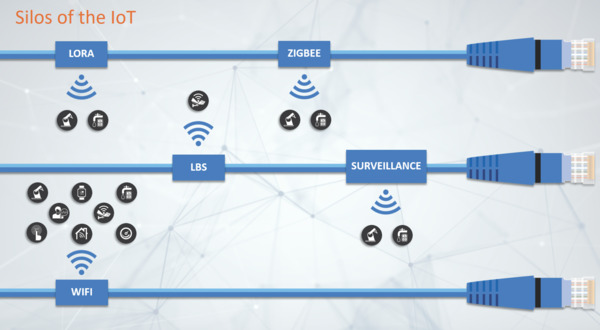
Today’s fragmented ecosystem of standards, devices, and services slows enterprise IoT deployments. Even successful deployments focus primarily on a single use case, such as location-based services or surveillance, or are locked to a single standard such as
Zigbee or
LoRa. The result: these deployments require a redundant network infrastructure, may be missing critical security mechanisms, and require extensive systems integration to interoperate with other IoT solutions.
Top Three Challenges of Enterprise IoT Adoption
- Countless Standards. More than 15 billion Wi-Fi radios were installed into more than 6.8 billion devices in 2016, making Wi-Fi one of the most prolific technologies in the world. However, Wi-Fi’s power requirements and range constraints limit its suitability to IoT sensors and tags that are meant to run on batteries or to relay information over long distances. While Zigbee, LoRa, Bluetooth Low Energy (BLE) and other associated IoT standards address power concerns, they are not as ubiquitously deployed. Additionally, low power WAN (LPWAN), IPv6 over Low-Power Wireless Personal Area Networks (6LowPAN), and alternative 802.15.4 based standards continue to contend for recognition.
- Weak Security. IoT endpoints are often resource-constrained, “headless,” non-IP devices that lack the hardware capabilities to support security best-practices such as digital certificates. Physical-layer security such as the 128-bit AES encryption provided by 802.15.4 standards-compliant ASICs offers but one layer of protection. Given the less-than-ideal security capabilities of today’s IoT endpoints, breach detection is difficult and the cost to determine such a breach can often eclipse the cost to replace these simple beacons and tags.
- Lack of Interoperability. In a smart home, a thermostat must talk to the HVAC system, a daylight sensor must talk to lights and window shades, and air filters must alert us when a filter replacement is needed. Communication between devices is critical if the IoT is to have any impact on our daily lives or within our enterprises. Today’s IoT silos can require extensive systems integration to allow inter-device communication between different IoT solutions, thus making enterprise adoption all the more difficult.
Countless Standards
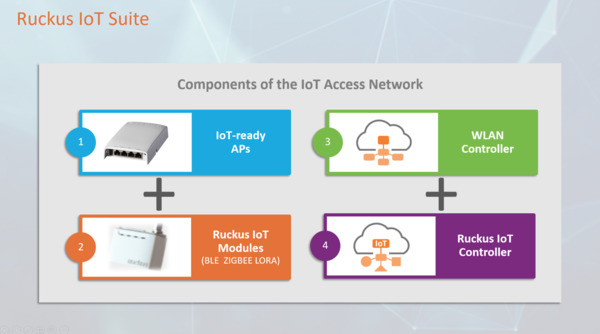
Announced on February 21, The Ruckus IoT Suite allows enterprises to build an
IoT access network that supports both Wi-Fi and non-Wi-Fi IoT endpoints with a shared multi-standard access network that reuses the same device onboarding, security, and management network infrastructure used for today’s wired and wireless LANs. The Ruckus IoT Suite comprises of four elements:
Weak Security
Security is a top concern contributing to IoT deployment delays. Addressing IoT security requires a multi-layered approach. The Ruckus IoT Suite bundles security best-practices, including:
- Digital certificates
- Traffic isolation
- Physical security
- Encryption
Because the Ruckus IoT Suite works within the existing LAN/WLAN infrastructure, past and ongoing security infrastructure investments such as firewalls and triple-A services remain usable.
Lack of Interoperability
By building on top of the Ruckus IoT Suite, neither the IoT solution providers nor their customers need to rollout device-specific-only networks. The Ruckus IoT Suite serves as the access layer connecting their IoT things to their respective IoT services.
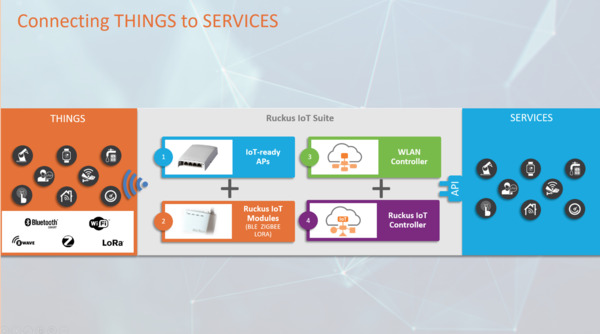
By leveraging and extending the existing network infrastructure with multi-radio standards support, multi-layered IoT security, and cross-solution rules management the Ruckus IoT Suite can address a variety of IoT requirements for varied use cases.
Connecting IoT Silos and Services
For enterprises, deploying an IoT access network that supports multi-radio standards over a converged network infrastructure is only the first step in a long journey to go beyond just connecting people and their devices. By implementing multi-layered security, benefits derived from deploying IoT devices and services outweigh the security risks introduced by new technology. And with support for cross-solution device communications and the ability to connect IoT cloud services, all while leveraging existing network investments, 2018 is shaping up to be a great year to drive enterprise IoT adoption, moving beyond the IoT hyperbole.


 By leveraging and extending the existing network infrastructure with multi-radio standards support, multi-layered IoT security, and cross-solution rules management the Ruckus IoT Suite can address a variety of IoT requirements for varied use cases.
By leveraging and extending the existing network infrastructure with multi-radio standards support, multi-layered IoT security, and cross-solution rules management the Ruckus IoT Suite can address a variety of IoT requirements for varied use cases.















